Jasper Wang’s blog
In a quiet place, a person can hear his own thoughts.
Packet Analysis / ARP Spoofing
Preparations - Identify who is on the network
I can not run Herbivore on Mac, probably because of the system doesn’t allow. If running this on a ITP macbook, then worked.
So, I run the command arp -a in the terminal. And got the result like this.
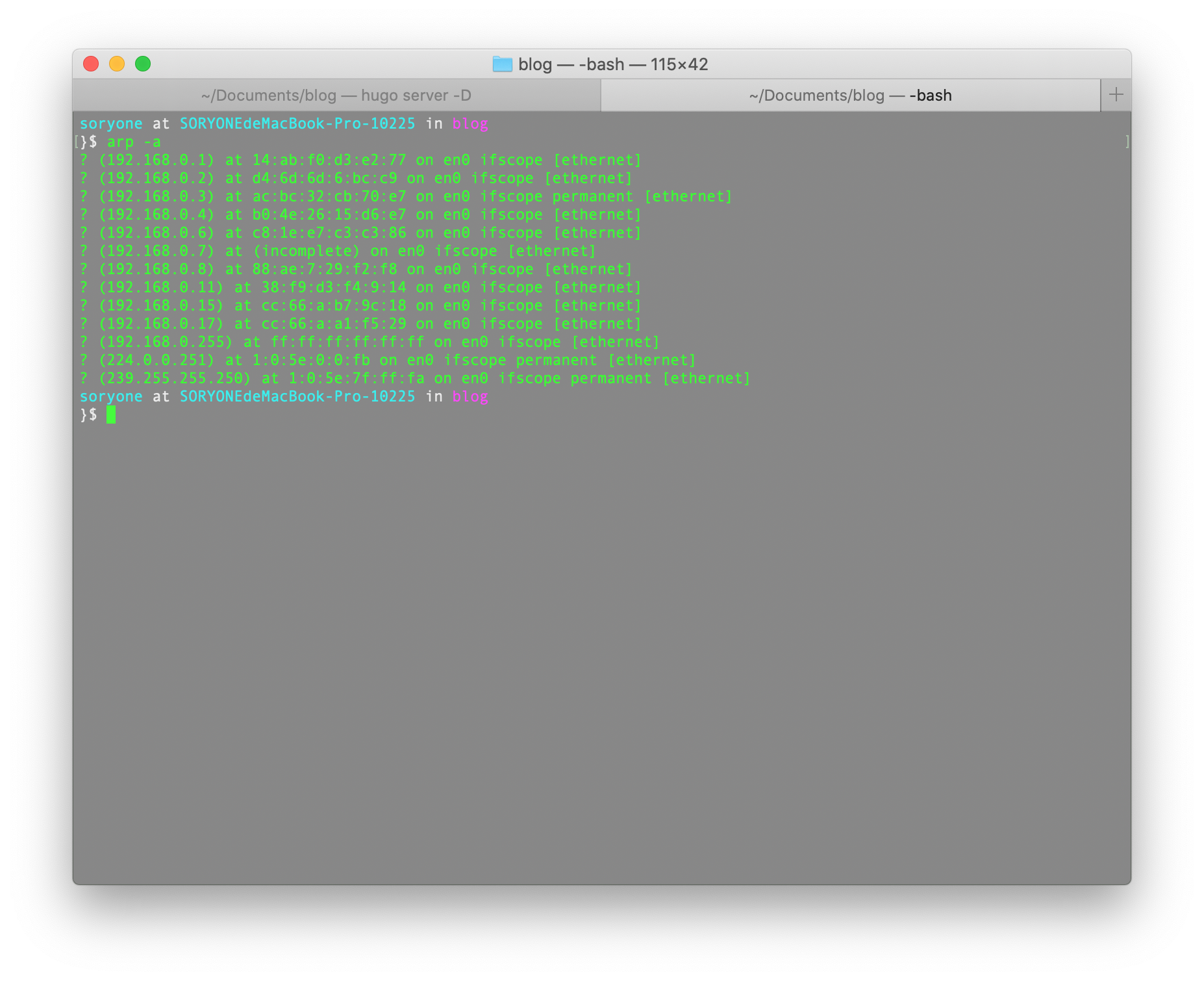
A lot of devices running on my home network. To figure out them easily, I used a software to help with me a little bit.
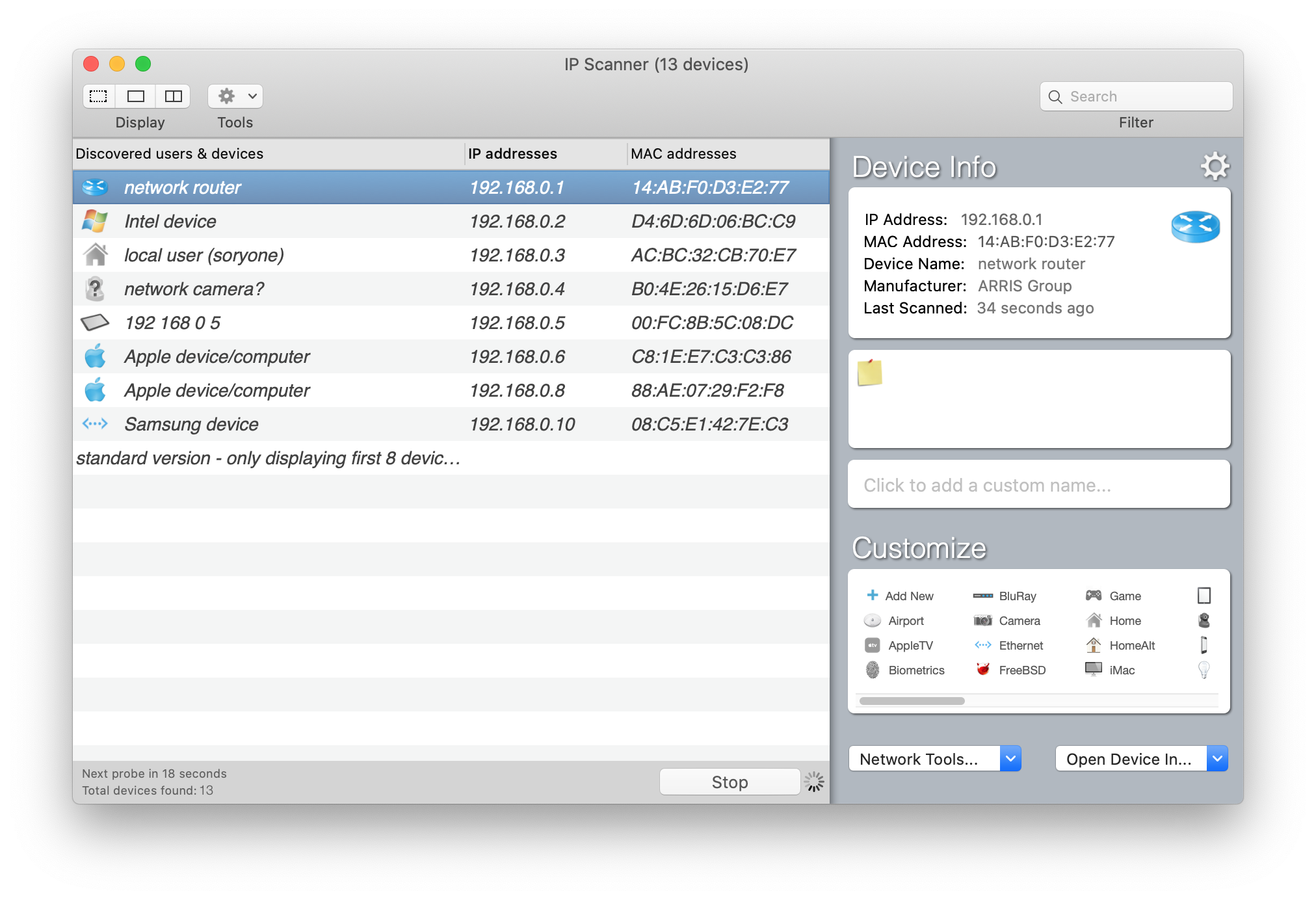
So I can basicly know what are thoes devices, my amzon alexa is also listed, the ip ends with 05. Surprisingly, I find out my roommate is running a camera in his room, which he never told me before.
Another way to get own ip address is ifconfig | grep "inet " | grep -v 127.0.0.1. And it returns me like this : inet 192.168.0.3 netmask 0xffffff00 broadcast 192.168.0.255.
Start Sniffing
The first thing I did is to track the arp protocall.
Address Resolution Protocol (ARP) is a procedure for mapping a dynamic Internet Protocol address (IP address) to a permanent physical machine address in a local area network (LAN). The physical machine address is also known as a Media Access Control or MAC address.
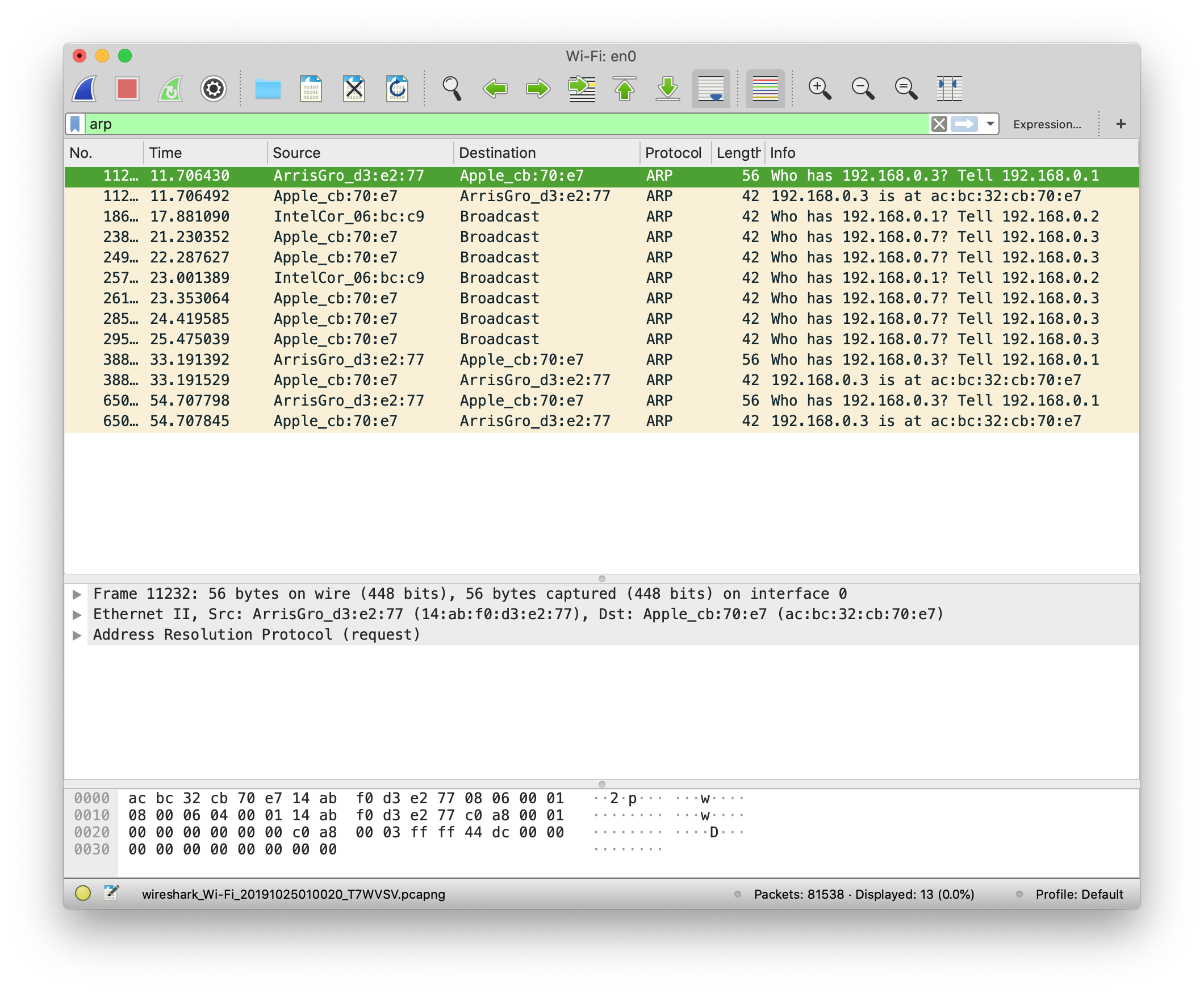
The way they talk is also interesting: ARP broadcasts a request packet to all the machines on the LAN and asks if any of the machines know they are using that particular IP address. When a machine recognizes the IP address as its own, it sends a reply so ARP can update the cache for future reference and proceed with the communication.
HTTP Traffic
Then I start to look at my HTTP packets. One thing I am really interested in is to test the security of the website. Cause we discussed about the HTTP and HTTPS before. So I want to test if HTTP is really that less security.
I find a lot of websites that I used to go in China several years ago, like my middle school website, local news website and the largest library in my home status. I found they are all using the HTTP instead of the HTTPS.
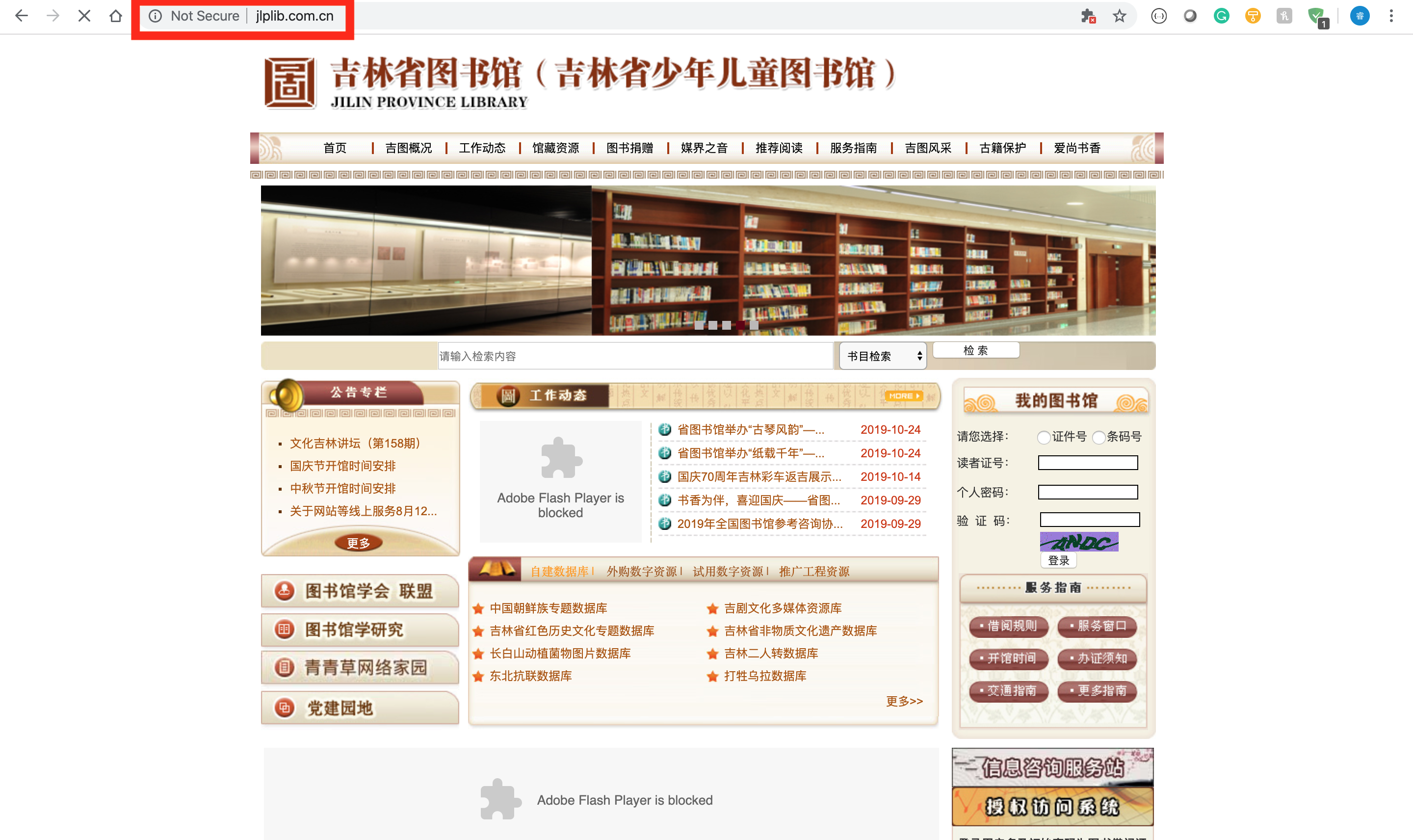
The library webite has a user login system, which allows the readers to find and reserve books on line, and it contains a lot of user informations, like your check out history, your id card number, phone number. I use my mother’s account as an example.
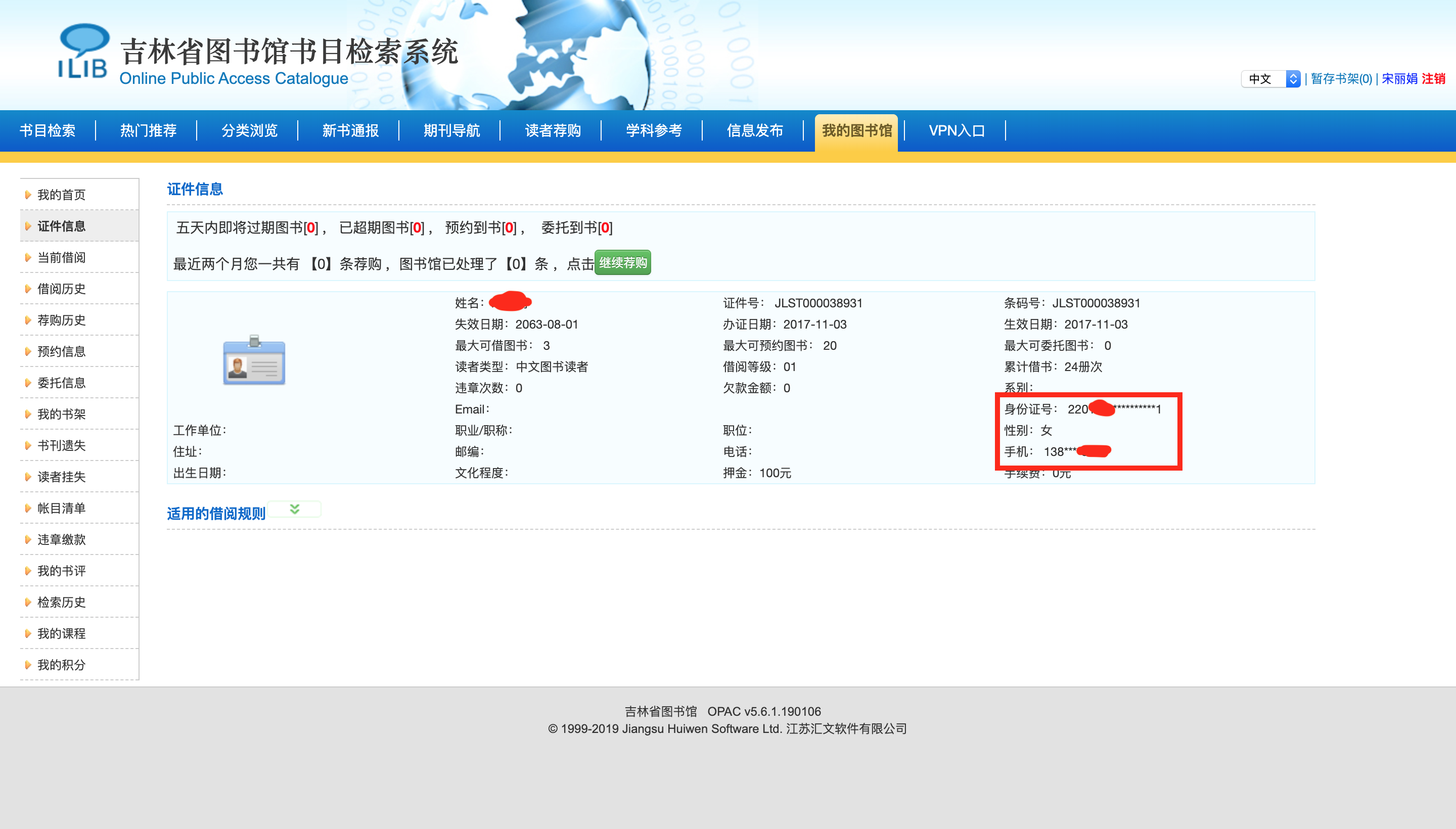
So I want to try if I can sniff the HTTP POST request packet when I am logging in to my account.
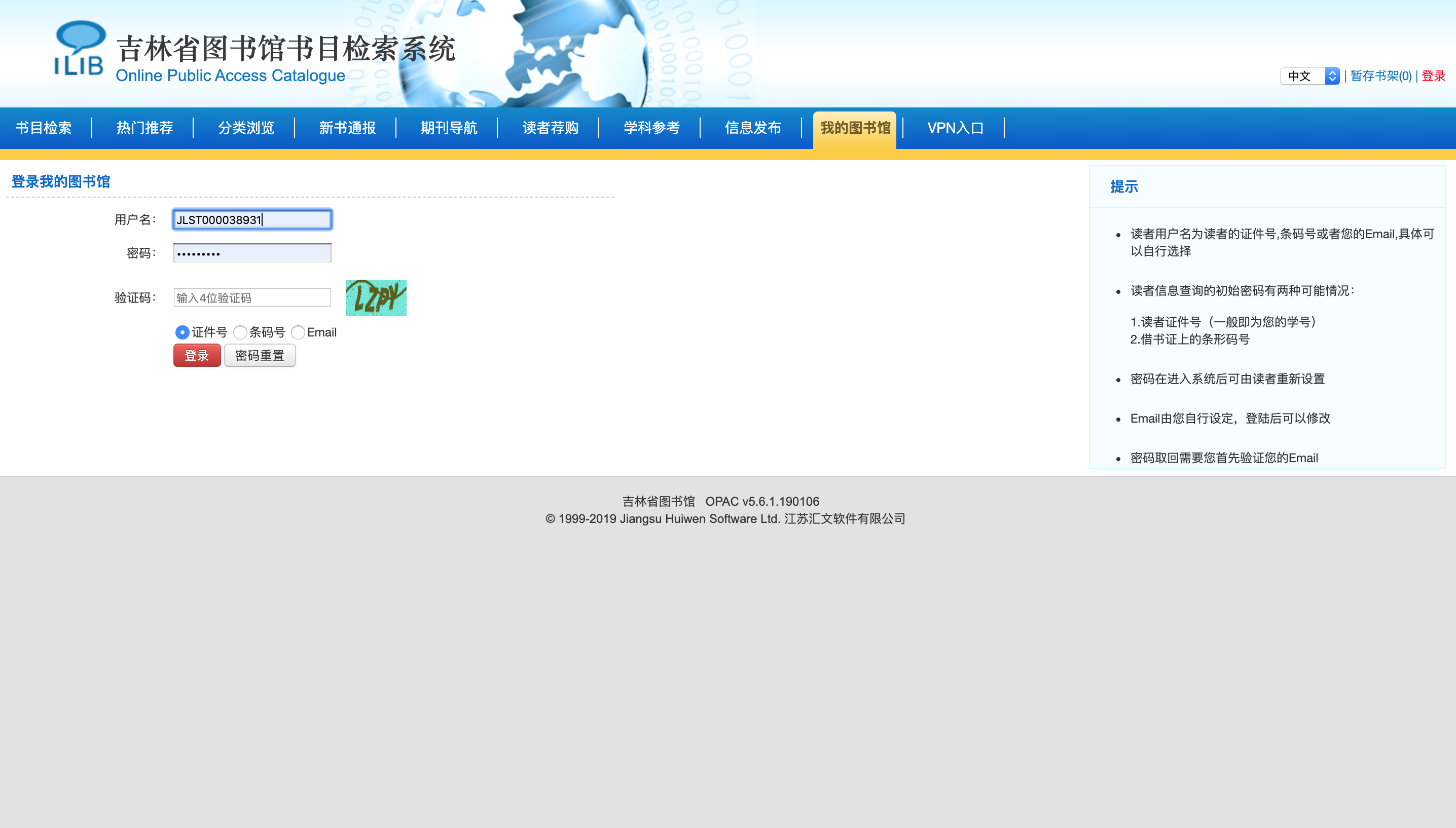
Use flitter to get the HTTP packets.
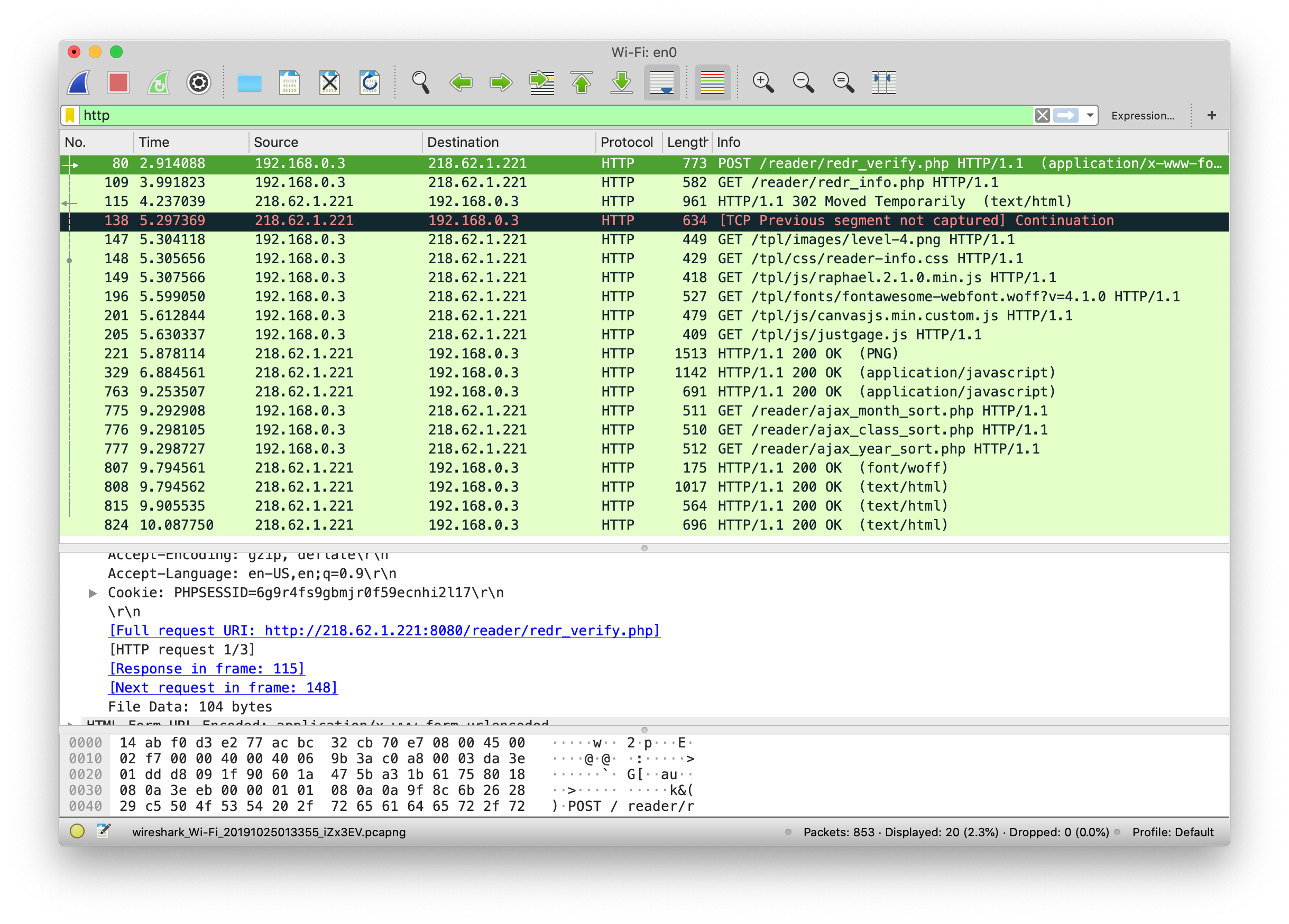
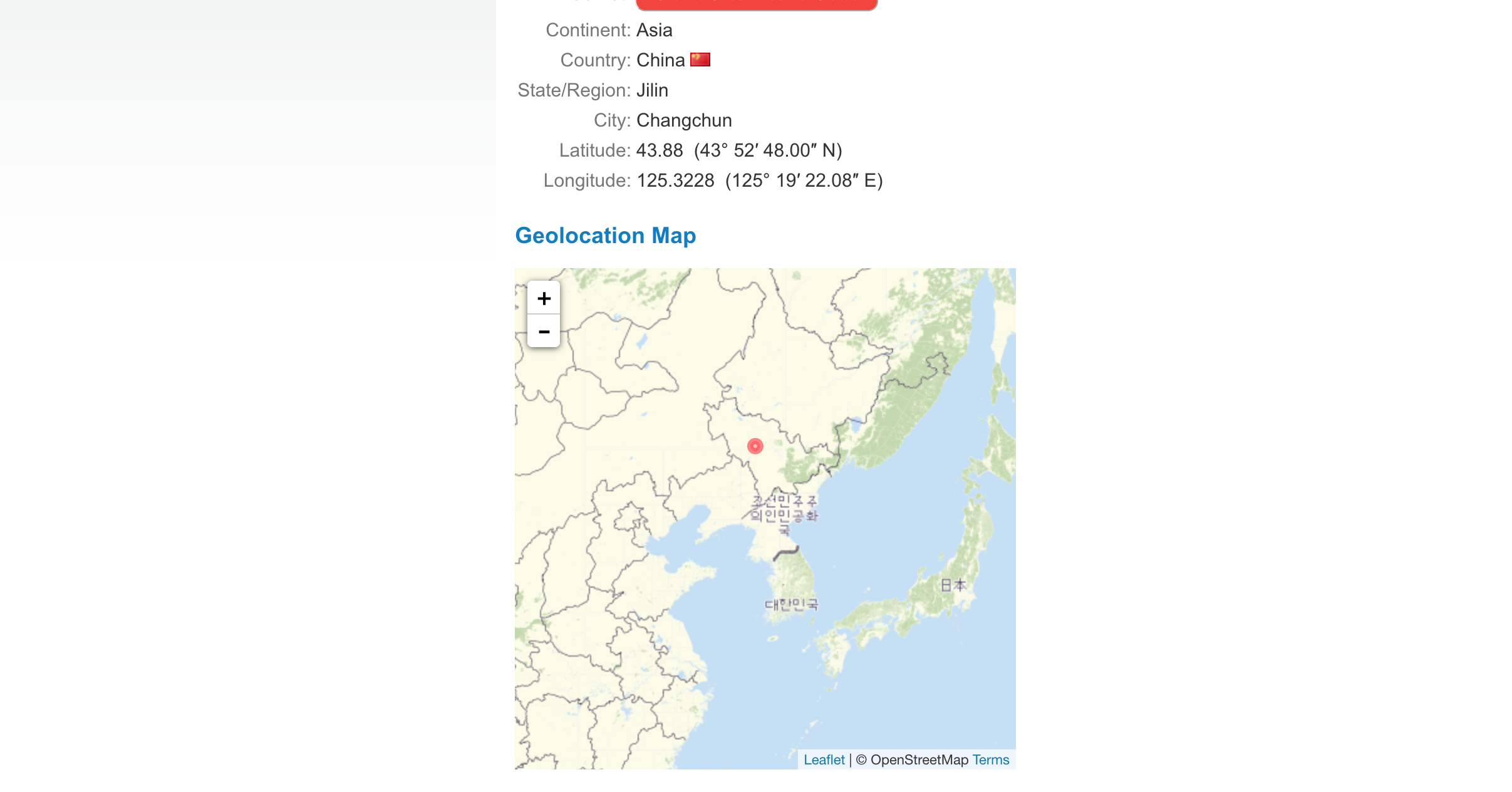
Clearly, the first one is the one I want, the packet is sent from my ip - 192.168.0.3, the destination is 218.62.1.221. I doubled checked that IP to make sure it is the library’s IP.
I can see the detail of this packet below.
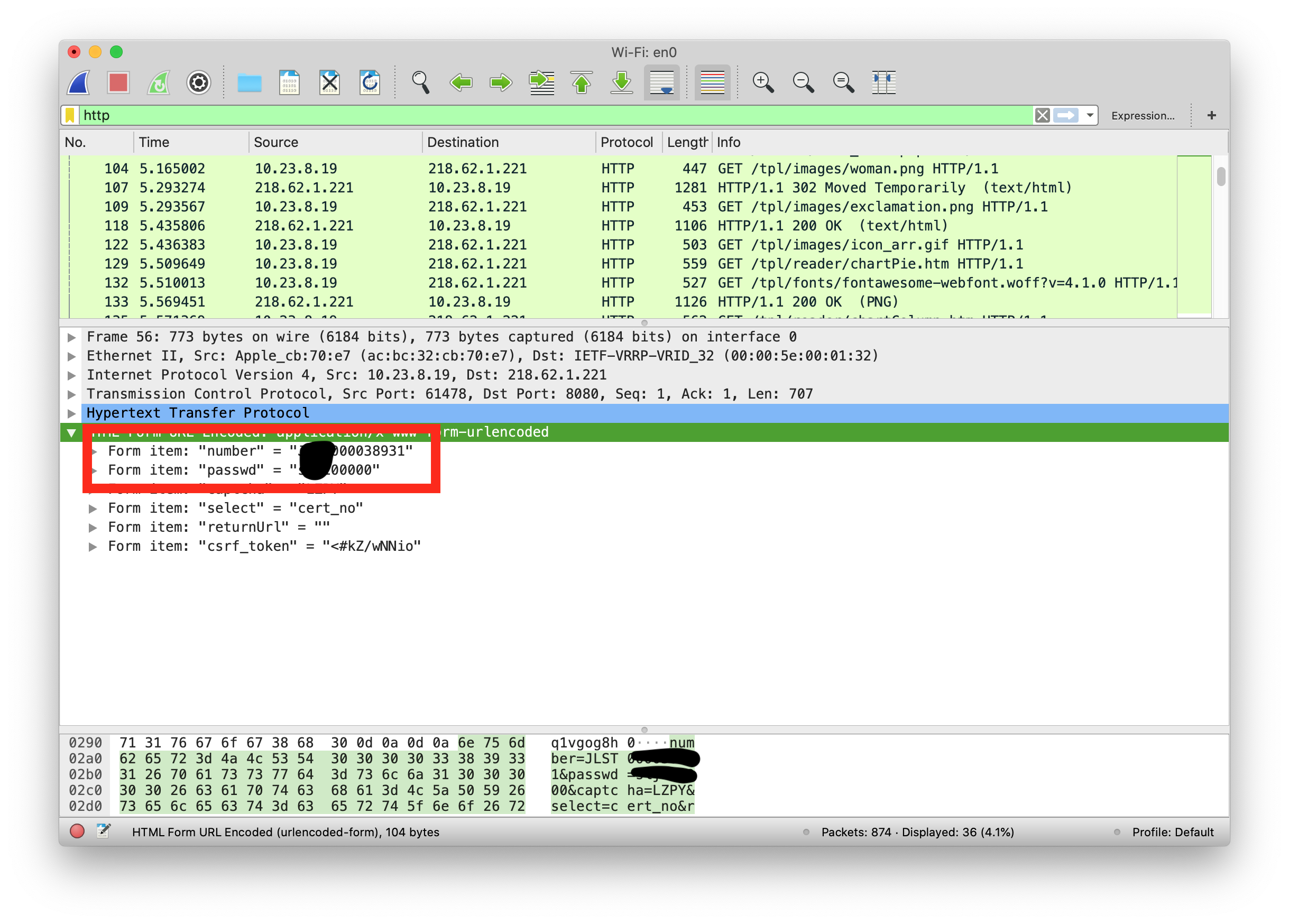
Also I can follow the cookie. The username and the password are showing here.

So it’s really easy to get user’s informations by sniffing their packets.
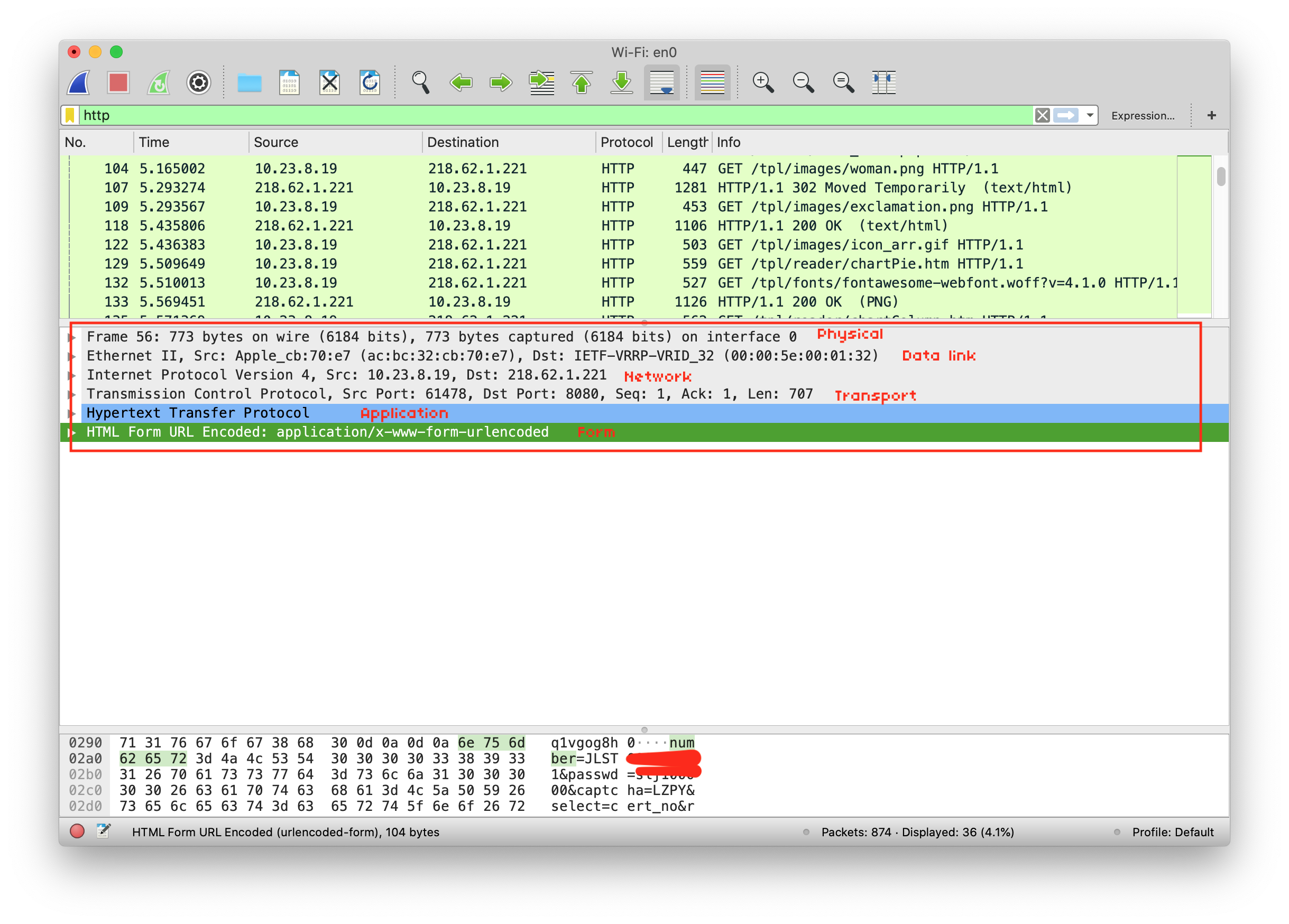
The result also shows the OSI layer. That’s really helpful.
ARP Spoofing
At this point, I can’t help thinking about how other people could get my informations using the packets sniffing. After a conversation with Tom, I know that is called ARP Spoofing or ARP Attacking. Then, I did some researches on this topic.
ARP is a protocal to map the ip address to the mac address.
Every laptop with an Ethernet has at least one ARP table. To save the known ip addresses and mac addresses. Pretty much the same as post code and address for mailing.
ARP spoofing is to confuse the target that I ( bad guy ) am the destiantion that your packets are going to reach. Which is not true, because you want your packets go to the router, and then go through the internet to a remote router.
By doing this, every packets the target sent will first go through my device, then go the router, you also need to be a carrier.
Once I garther the packets, I can do packets analysis like what I did in wireshark.
Very easy to understand. And that is the famous man-in-the-middle attack.
How to get my roomate’s packets?
So, how to do that in practical? Can everybody do that? Basicly, they can.
I first reserach some blogs and videos about how to do the Arp spoofing. But most of them are doing that on a Kali Linux system, it doesn’t work on Mac.
Finally, I find one way to do that on mac by running a Python script. Need to install a lot things and it takes a long time to get settled. And I did it.
Now, it’s time to test it. I ask my roomate if I can test it with his laptop, and he is so glad to join me.
I can get his current ip easily by either using the
arp -acommand or using an ip software.run the script in Terminal like this:
python SCRIPTNAME -t MYROOMMATE'SIP -g ROUTER'SIP -i NETWORKINTERFACE --sniff.Then the my laptop start to taking to my roomate’s laptop.
Start the wireshark
get all the packets from him
I ask him to the same test as I did, which is logging into my library account. And I got the same result.
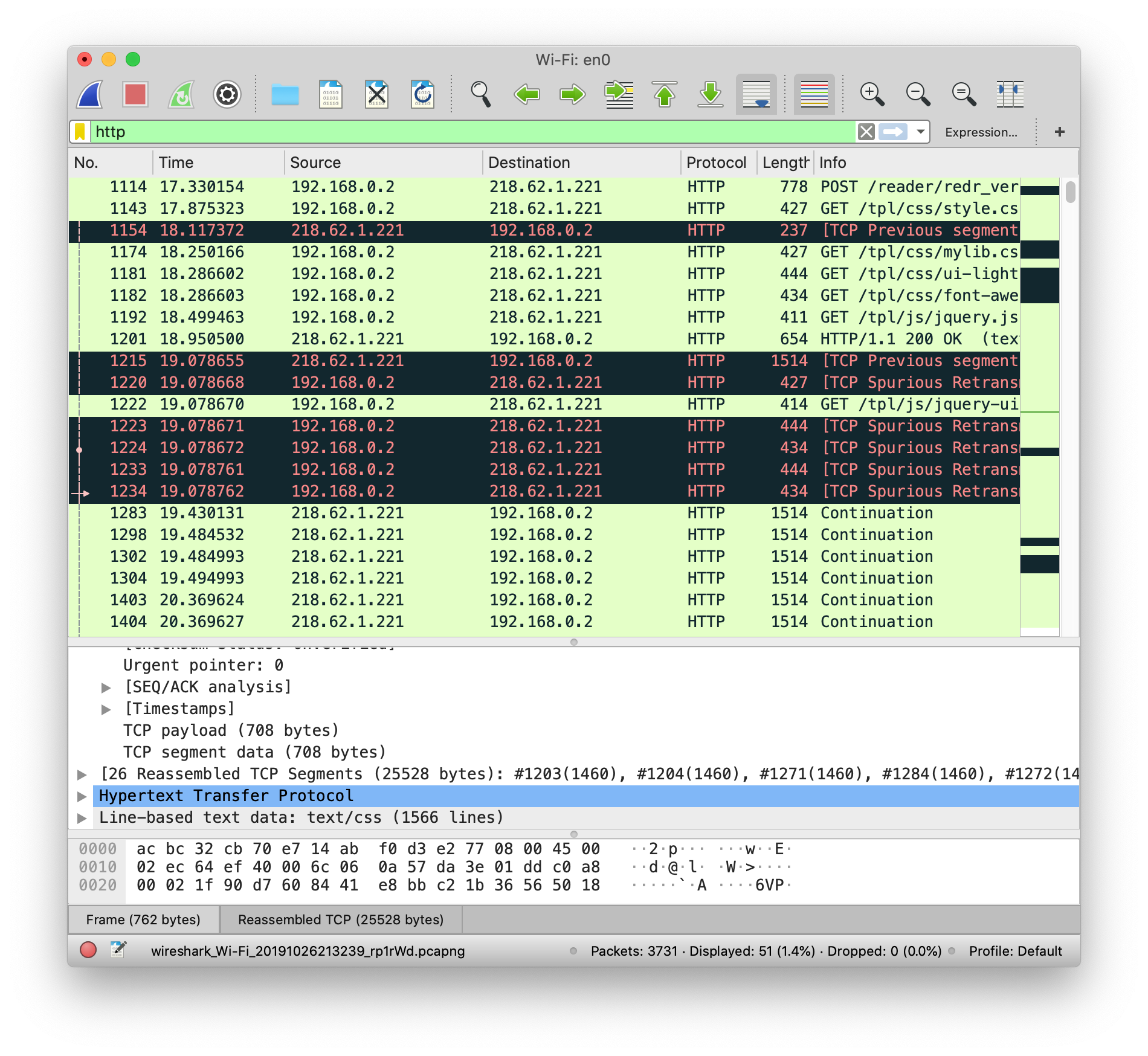
Which proves the point HTTP is not safe.
Then, he wants to go the offical website of Norh Korean, And he wants me to track him. An we did it.
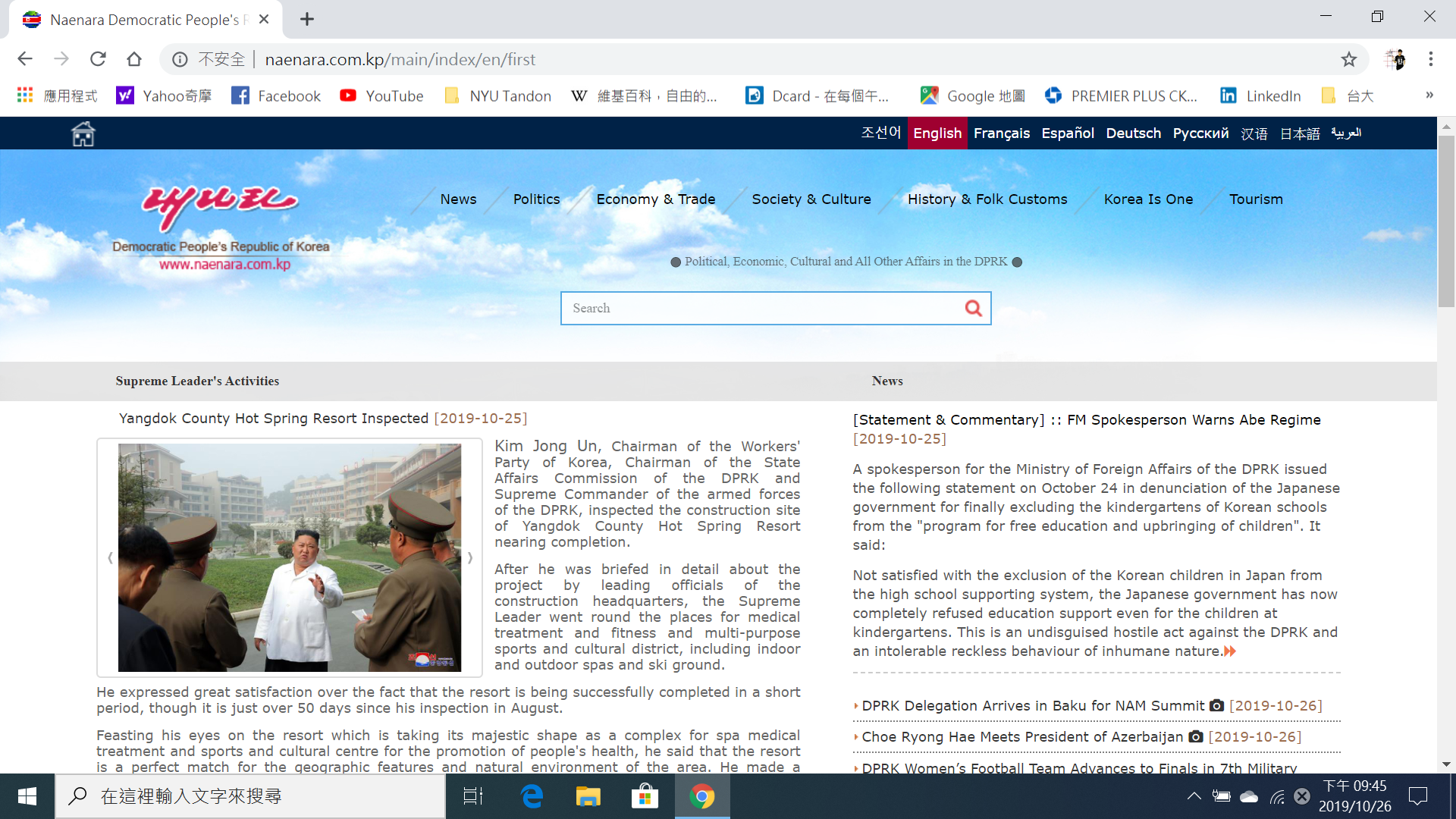

Double check, to make sure the server is in North Korea.
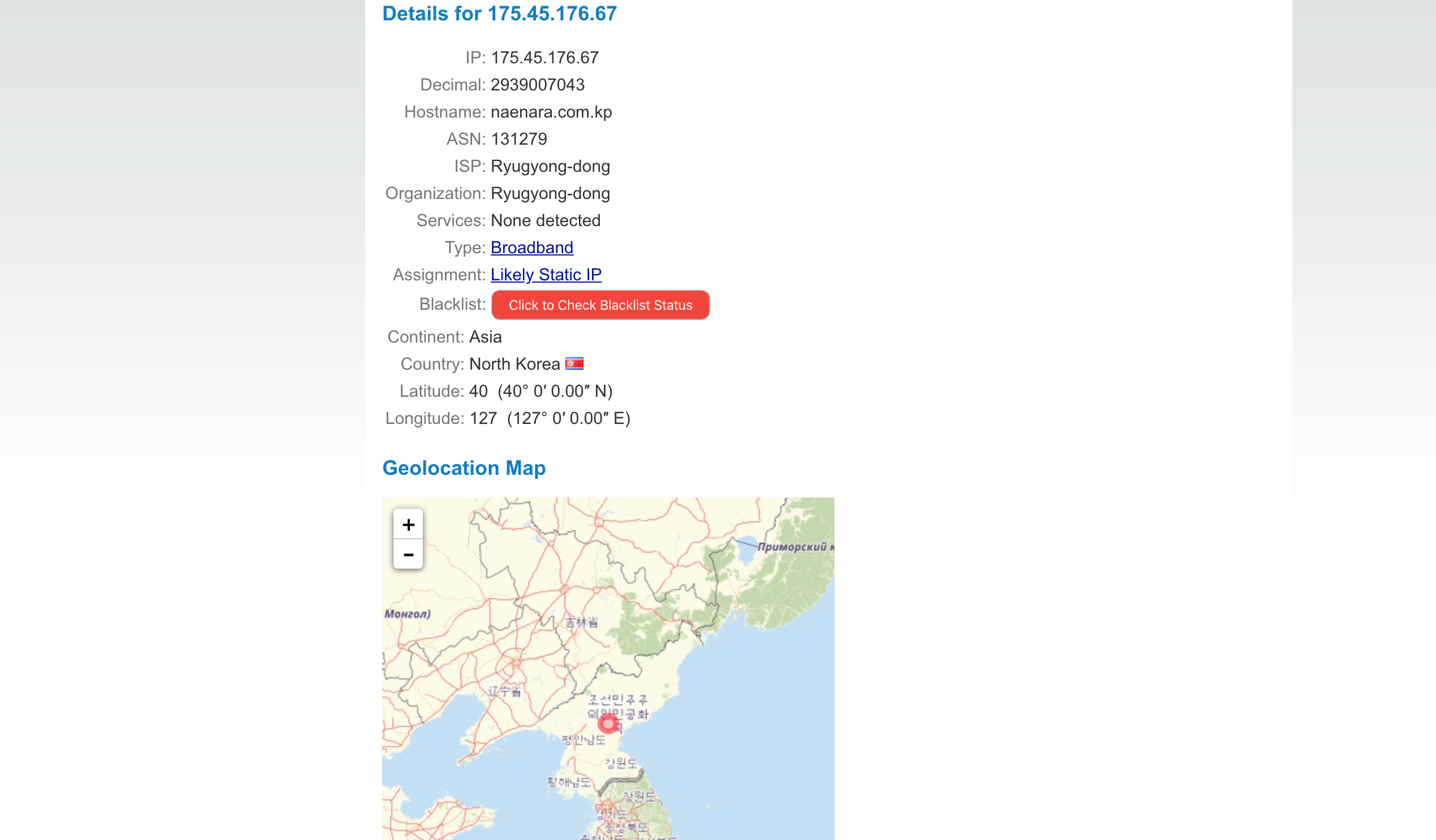
Here I sniff a POST request, I think he searched something on that web.

I can’t see the content he entered, I don’t know why. Need to ask Tom.
I can also sniff the image result from the packet, an save the image to my local machine.
Anyway, I successful “fooled” my roommates’s laptop, and get the information when he goes to a unsafe web.
So, I realized that connecting to a wifi in public is at risk, and don’t put any sensitive informations on an unsafe website, even sometime, you see it is a HTTPS web, but that doesn’t mean the data are all transfered with encryption.
SFTP Sniffing
lastly, I want see how ssh works, so I connect to my server on digtial ocean.Start sniffing, then upload a folder to the droplet.
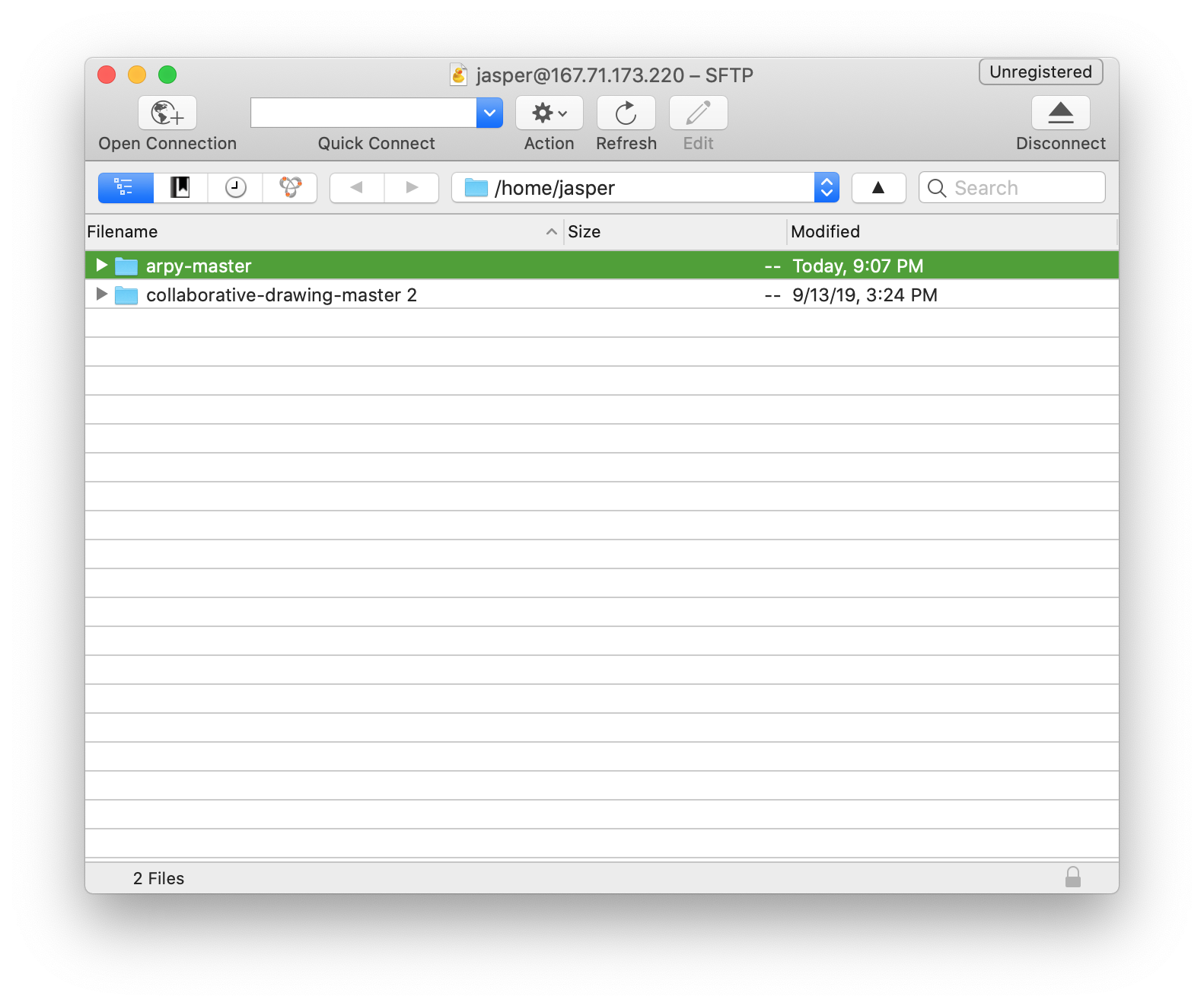

From the result, I can see every packet send from my local laptop to the remote server. And the data are all Encrypted.
Prove that SSH is actually a safe method.